Introduction
In today’s digitally driven world, contact centers serve as pivotal hubs for businesses to interact with customers. However, amidst the myriad of conversations lies a treasure trove of sensitive information, making data security a top priority. According to a recent study by Statista, the global call center market is projected to reach $496 billion by 2027, underscoring the immense volume of data being exchanged daily. With this exponential growth comes the pressing need for robust security measures, and one such indispensable tool is redaction.
What is Redaction?
Redaction, in its essence, is the process of selectively removing or obscuring sensitive information from documents or media, while still maintaining their usability and integrity. It’s akin to wielding a digital black marker to shield confidential details from prying eyes.
In contact centers, where personal identifiable information (PII) flows freely, redaction emerges as a formidable shield against data breaches and regulatory non-compliance. It’s not just about concealing data; it’s about fortifying the fortress of confidentiality, instilling trust among customers, and upholding legal obligations.
Why Redaction is Important?
Redaction is a security guiding light in the maze of contact center operations, helping businesses navigate the harsh seas of fraud prevention, data protection, and regulatory compliance.
Compliance: Meeting Regulatory Standards
Regulatory bodies such as GDPR, HIPAA, and PCI DSS have set stringent guidelines regarding the handling of sensitive information. Failure to comply can lead to hefty fines and tarnished reputations. According to a report by IBM, the average cost of a data breach is estimated to be $4.24 million. Redaction acts as a proactive measure, ensuring adherence to these mandates and shielding organizations from regulatory repercussions.
Data Security: Protecting Sensitive Information
Nowadays, with everything being digitized, data is a prized possession, coveted by both legitimate businesses and nefarious entities. Contact centers serve as prime targets, housing a treasure trove of customer data ripe for exploitation. Redaction acts as a formidable barrier, safeguarding sensitive information from prying eyes and malicious actors. As per Verizon’s 2021 Data Breach Investigations Report, 85% of breaches involved the exploitation of human vulnerabilities, emphasizing the critical role of data obscuration in fortifying data defenses.
Prevention of Fraud: Safeguarding Against Malicious Intentions
Fraudsters lurk in the shadows, waiting to pounce on unsuspecting victims. Contact centers, with their vast repository of personal and financial data, are prime hunting grounds. Redaction serves as a preemptive strike, obscuring vital details and thwarting fraudulent activities before they can inflict harm. According to the Federal Trade Commission, imposter scams alone accounted for $328 million in losses in 2020. Data obscuration emerges as a stalwart guardian, ensuring that sensitive information remains beyond the reach of fraudsters’ grasp.
Understanding what Information to Redact
Before embarking on the redaction journey, it’s imperative to decipher the labyrinth of data and identify the jewels amidst the rubble.
Identifying Sensitive Data:
Sensitive data comes in various shapes and forms, ranging from names and addresses to social security numbers and credit card details. It’s the lifeblood of contact centers, fueling operations and nurturing customer relationships. However, it’s also a double-edged sword, capable of wreaking havoc if mishandled. Redaction shines a spotlight on these hidden gems, allowing organizations to identify and safeguard them with precision.
Examples of Information Requiring Redaction:
- Personal Identifiable Information (PII): Names, addresses, phone numbers, and social security numbers.
- Financial Data: Credit card numbers, bank account details, and transaction history.
- Health Information: Medical records, prescription details, and health insurance information.
- Confidential Conversations: Recorded calls, chat transcripts, and email communications.
- Intellectual Property: Trade secrets, proprietary algorithms, and product designs.
Overview of Redaction Processes
Redaction is not merely a manual task but a nuanced process facilitated by cutting-edge technology and meticulous methodologies. It typically involves the following steps:
- Identification: Scouring documents and media to pinpoint sensitive information requiring Removal/erasure.
- Selection: Choosing the appropriate technique based on the type and context of the information.
- Application: Implementing tools and techniques to obscure or remove sensitive data securely.
- Review: Conducting thorough quality checks to ensure the effectiveness and accuracy of efforts.
- Validation: Verifying compliance with regulatory standards and organizational policies to mitigate risks.
How does Redaction Works? Tools and Techniques.
Armed with a deeper understanding of redaction’s significance and its various forms, let’s delve into the operational mechanisms that power this indispensable security measure.
Tools for Efficient Redaction:
Numerous tools and software solutions have arisen in the constantly changing field of cybersecurity, each with its own set of features and functionalities. Among the well-known instruments are:
Adobe Acrobat Pro:
A versatile tool offering comprehensive redaction capabilities for PDF documents, including text, images, and metadata.
Redact-it Desktop:
A user-friendly solution equipped with advanced redaction algorithms for text, images, and audiovisual content.
iScrub:
A specialized tool designed for scrubbing metadata from documents and media to safeguard against data leaks.
Blackout:
An open-source redaction tool offering flexible customization options and seamless integration with existing workflows.
Techniques for Redacting Different Types of Information
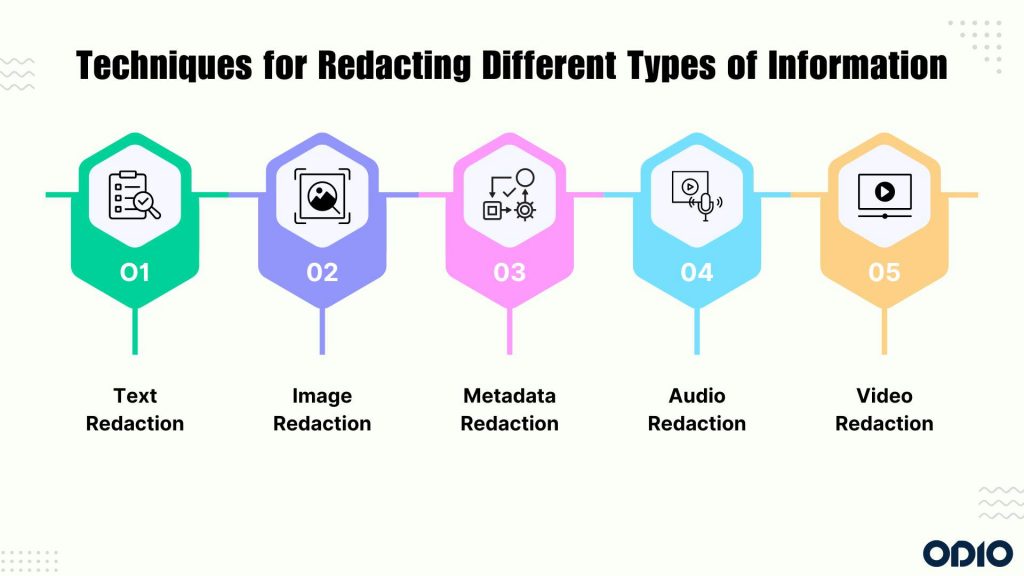
Effective redaction hinges on employing the right techniques for the job, ensuring maximum security and usability. It is not a one-size-fits-all solution; rather, it’s a multifaceted toolkit comprising various techniques tailored to specific needs. Here are some tried-and-tested methods for redacting different types of information:
- Text Redaction: It involves obscuring sensitive information within textual documents, such as contracts, emails, and reports. It can range from simple blackouts to more sophisticated methods like encryption and tokenization.
- Image Redaction: Images often contain hidden nuggets of information that can compromise security. You can employ techniques such as blurring, pixelating, overlaying ,and/or cropping to obscure identifiable elements within images.
- Metadata Redaction: Metadata lurks beneath the surface, harboring a wealth of information about a document’s origin, authorship, and history. It involves stripping these digital footprints to ensure anonymity and confidentiality. You can leverage metadata scrubbing tools to remove identifying information embedded within documents and media files.
- Audio Redaction: In the realm of recorded calls and voicemails, audio redaction plays a pivotal role in concealing sensitive conversations and personal details. You can use audio editing software to mute, bleep, or distort segments containing sensitive conversations or personal details.
- Video Redaction: Videos capture moments in time, but they also harbor potential risks if mishandled. Use video editing tools to blur faces, license plates, or other identifying features within video footage without compromising visual clarity.
AI driven Redaction
As we have learned, redaction involves a variety of techniques to safeguard sensitive data, but modern advancements have introduced a game-changer: leveraging the power of AI. Artificial Intelligence (AI) technologies have revolutionized data obscuration processes, offering unprecedented efficiency, accuracy, and scalability.
Contact centers can automate the identification and redaction of sensitive data from enormous amounts of records, documents, and media assets by utilizing AI algorithms. Artificial intelligence (AI)-driven data obscuration solutions reduce manual labor and human error by intelligently scanning, analyzing, and redacting sensitive content. They do this by utilizing machine learning and natural language processing capabilities.
Moreover, AI-driven solutions continuously learn and adapt to evolving data privacy regulations and emerging threats, ensuring ongoing compliance and proactive risk mitigation. With AI, contact centers can enhance their redaction practices, streamline operations, and stay ahead of the curve in safeguarding sensitive information.
Implementing the Right Redaction Strategy
As the adage goes, “Failing to plan is planning to fail.” This rings especially true in the realm of redaction, where a well-thought-out strategy can spell the difference between fortification and vulnerability.
Assessing Redaction Needs:
Before diving headlong into the redaction process, organizations must conduct a comprehensive assessment of their data Removal needs, taking into account factors such as:
- Volume and Variety of Data: Evaluate the types and volume of sensitive information handled by the organization across various channels.
- Regulatory Requirements: Determine the specific regulations and compliance standards applicable to the organization’s industry and geographic location.
- Risk Profile: Identify potential threats and vulnerabilities that may compromise the security and confidentiality of sensitive information.
- Operational Considerations: Consider the practical implications on existing workflows, systems, and resources.
By conducting a thorough assessment, organizations can gain invaluable insights into their information obscuration requirements, paving the way for informed decision-making and strategic planning.
Developing Redaction Policies and Procedures:
With a clear understanding of data Removal needs in hand, the next step is to develop robust policies and procedures governing redaction practices within the organization. Key components of effective redaction policies include:
- Scope and Objectives: Clearly define the scope and objectives of the redaction policy, outlining its purpose, goals, and intended outcomes.
- Roles and Responsibilities: Assign roles and responsibilities to individuals or teams responsible for overseeing and executing redaction activities.
- Redaction Guidelines: Establish clear guidelines and best practices for identifying, prioritizing, and implementing redaction across different types of information and media.
- Quality Assurance: Implement mechanisms for quality assurance and review to ensure the accuracy, completeness, and effectiveness of redaction efforts.
- Training and Awareness: Provide comprehensive training and awareness programs to educate staff on redaction protocols, tools, and techniques.
By formalizing redaction policies and procedures, organizations can streamline operations, mitigate risks, and ensure consistency and compliance across the board.
Training Staff on Redaction Protocols:
As the last line of defense, frontline staff play a pivotal role in executing redaction protocols effectively. Providing them with the necessary knowledge, skills, and resources is paramount to the success of any redaction initiative. Training programs should cover:
- Redaction Techniques: Educate staff on the various data obscuration techniques and tools available, emphasizing their proper usage and application.
- Regulatory Compliance: Familiarize staff with relevant regulatory requirements and organizational policies governing information removal/obscuration practices.
- Risk Awareness: Raise awareness about the importance of data obscuration in safeguarding sensitive information and mitigating potential risks.
- Practical Exercises: Conduct hands-on exercises and simulations to reinforce learning and build proficiency in data removal/erasure skills.
- Ongoing Support: Provide ongoing support and resources to assist staff in overcoming challenges and addressing concerns.
By empowering staff with the knowledge and skills needed to navigate the intricacies of redaction, organizations can foster a culture of compliance, accountability, and vigilance.
Conclusion
Redaction appears as a ray of hope in the constantly changing world of contact center operations, where data is king and risks are everywhere. It provides protection, compliance, and peace of mind. Its importance cannot be emphasized, as it serves to protect private data and strengthen anti-fraud measures.
As the digital landscape continues to evolve and threats evolve in tandem, the question remains: Are you ready to fortify your defenses and embark on the journey towards a safer, more secure future?
Thank you for reading. We hope this blog has been helpful in providing you with valuable information. Share your thoughts in the comments to have a conversation on why redaction is important for your contact center. For more insightful blogs like this, please follow our blogs at Odio.

Leave a Reply